Why Open-Source? Power Of Open-Source
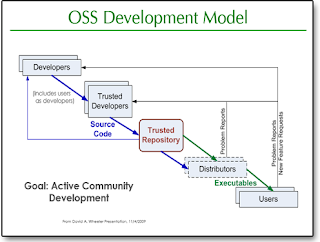
Open-source software (OSS) is computer software with its source code made available with a license in which the copyright holder provides the rights to study, change, and distribute the software to anyone and for any purpose. Open source developers choose to make the source code of their software publicly available for the good of the community and to publish their software with an open source license – meaning that other developers can see how it works and add to it. It is software developed by and for the user community. Open source projects provide tremendous opportunities for developers to share and learn through collaboration. Find colleagues for your project or join an existing effort. Contributions aren't limited to code, as projects need a diverse range of skills. Many of the world’s most successful open source projects have their roots in the academy. Participation extends beyond adoption and development, and now includes a wide variety of academic programs and researc



